In our regular series The inside story x 3, experts from the Plan.Net group explain a current topic from the digital world from different perspectives. What does it mean for your grandma or your agency colleague? And what does the customer – in other words, a company – get out of it?
As we continue to take advantage of online services, apps, and websites of all kinds, we are creating enormous quantities of data. This data is often stored in clouds and can be linked back to each and every user. At the same time, most Internet users are failing to take the protection of their data as seriously as they should, while companies are often failing to keep up with the rapid pace of developments and resolve dangerous security vulnerabilities fast enough. Even policymakers have only recently reached the point of being able to enforce existing data protection laws.
A case currently receiving wide media coverage, in which a 20-year-old man is accused of spying on politicians and celebrities, shows just how easily data stored in the cloud can be used to infiltrate entire personal networks.
“No Grandma, you haven’t broken the Internet!”
Let’s admit it: who among us hasn’t been just a click away from a potential hacker attack? Even younger users are often tricked by false landing pages or phishing emails that invite them to reveal all of their data and passwords, together with those of their contacts. And net-savvy grandparents who have opted to embrace progress unfortunately aren’t safe either, as their grandchildren may have been kind enough to save all of the passwords to sites bookmarked in their browser. “It’s all just a click away, you see?”
Users are most commonly tricked by deceptively convincing emails that invite them to open an attachment or link. Once opened, a website asks the user to log in to their bank account for the purposes of authentication. If fallen for, this provides hackers with all of the access data they need to empty pension accounts and cause a great deal of upset. And as if this wasn’t enough, criminals are now able to purchase security vulnerabilities on the Dark Net, meaning that they no longer even need a hacker’s technical know-how in order to ply their trade online. Attacks of this kind are completely random, placing even unsuspecting grandmas at risk. No one solution is enough to protect against a threat as complex as this.
A first step in the right direction is using complex passwords and a password manager app – and, most importantly, only using one password per online service.
“Safety first – even in the ‘safety’ of your workplace”
As an Internet user, you aren’t only responsible for yourself, but also for the security of your colleagues and of the employer whose data you are working with. Backups of your own or your company smartphone are now often stored in a cloud automatically, which makes it almost impossible to prevent your colleagues’ data and contact information from being stored externally. If a hacker gains access to a personal account, such as Google Mail, Apple, or Facebook, this will give them automatic access to others’ business accounts and contact information, even though the company’s security standards have been followed.
One solution for this problem is provided by “sandboxes”, which manage the context of usage to help distinguish what is private from what is work-related. To begin with, however, businesses need to establish guidelines that make it clear which clouds are generally suitable to use and which should be avoided in a work-related context.
So what can my company do to properly counter this rapidly growing threat? Here too, your top priority is to not underestimate the human factor. Even the most complex technical safeguards can be rendered ineffective by one employee’s careless actions. Employees who use the Internet in their work should follow the same safety measures that apply to private users. For management this means that, in addition to the company making use of the available technical solutions, employees must also be trained regularly in the safe use of cloud services, smartphones, email accounts, and other tools. If a company provides goods or services over the Internet, there is always a danger that an attacker will succeed in hacking into its applications.
“But why on earth would anybody want to hack my company?”
Many clients, and small and medium-sized businesses in particular, underestimate the threat that hackers pose to them, asking: “Why on earth would anybody want to hack us? We’re far too small and insignificant.” The mass-hacks of today aren’t about hackers targeting specific victims, however. The Internet is home to search engines which, like Google, scan the entire Internet in order to catalogue the infrastructure that it uses, including the manufacturers of servers, routers, and so on, as well as the versions of software installed on them.
If a hacker knows that version 1.4 of web server software “A” contains a vulnerability that they could exploit, they’ll first run a search for the version online before launching an automated attack on all of the potential targets that the search engine suggests to them. This means that anybody present on the Internet can be identified by hackers – albeit indirectly – as a potential target. The only way of protecting yourself is to know the threat, and to invest in security for your system and training for your employees. In a live interview at CeBit 2017, Edward Snowden answered a question about how the Internet could be made a safer place. His response: “Everybody who contributes something to the Internet, whether via text, videos, apps, shops, cloud services, or similar, has an obligation to make their contribution as secure as possible.”
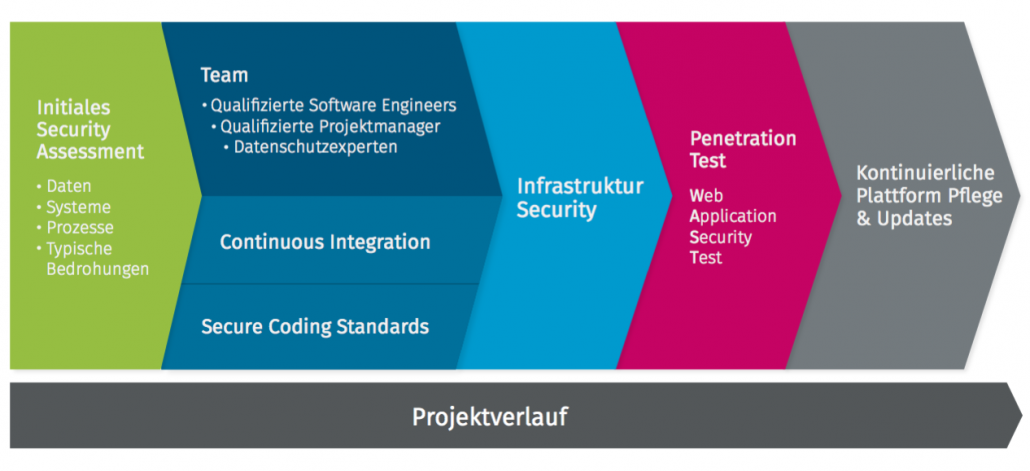
Even when using third-party software (software libraries) and other service providers, without which modern e-commerce platforms would cease to exist, it’s important to know the security risks. Only in this way can the risk be minimised of an apparently secure system being weakened via the unsecured “tunnel” of a third-party provider. Regular updates are an absolute necessity here. Regular pentesting of all system components is also a security precaution providers should take. Specifying security requirements (for example, in the form of secure coding guidelines) is also necessary nowadays when utilising implementation service providers, hosting companies and so on. As no software industry standard has been defined in this respect, it’s important to work with experts capable of defining a state-of-the-art standard. When service providers keep their cards close to their chests on this score, this is often the first indication of there being no long-term guarantee that security vulnerabilities will be resolved.